The Ice Spice Leak: Navigating Privacy In The Digital Age
Table of Contents
- Ice Spice: A Rising Star's Journey
- Understanding the "Ice Spice Leak" Context
- The Digital Landscape and the Illusion of Privacy
- Celebrity Exploitation and Content Rights in the Digital Age
- The Role of Online Communities and Fan Culture
- Ethical Implications of Consuming Leaked Content
- Legal Ramifications and Recourse for Victims
- Protecting Your Digital Footprint: Best Practices
- Conclusion: Towards a More Responsible Digital Future
Ice Spice: A Rising Star's Journey
Isis Gaston, professionally known as Ice Spice, has rapidly become one of the most talked-about figures in contemporary music. Hailing from the Bronx, New York, her unique blend of drill music with a laid-back, confident flow has captivated audiences worldwide. Her ascent to stardom began in 2022 with the viral success of her track "Munch (Feelin' U)," which quickly became a sensation on TikTok and other social media platforms. Her distinctive look, characterized by her fiery red curly hair, and her relatable yet audacious lyrics have cemented her status as a cultural icon. Ice Spice's journey is a testament to the power of viral marketing and the internet's ability to launch careers overnight. She represents a new generation of artists who leverage social media directly to connect with fans, build a brand, and disseminate their music without necessarily relying on traditional industry gatekeepers. This direct connection, while empowering, also exposes artists to unprecedented levels of scrutiny and vulnerability, making discussions around incidents like the alleged **Ice Spice leak** even more pertinent. Her rapid rise also highlights the intense pressure and public interest that can lead to invasive behaviors, including the search for and dissemination of private content.Personal Data and Biography
| Full Name | Isis Gaston |
| Stage Name | Ice Spice |
| Date of Birth | January 1, 2000 |
| Age | 24 years old (as of 2024) |
| Origin | Bronx, New York, U.S. |
| Genre | Hip Hop, Drill |
| Occupation | Rapper, Singer, Songwriter |
| Years Active | 2021–present |
| Notable Works | "Munch (Feelin' U)", "Bikini Bottom", "In Ha Mood", "Princess Diana" |
Understanding the "Ice Spice Leak" Context
The term "Ice Spice leak" has circulated across various online platforms, often without clear, verifiable evidence of what exactly was "leaked." In the digital age, a "leak" can range from genuinely private photos or videos being illicitly shared to unreleased music tracks, or even just rumors and unconfirmed snippets of information that gain traction. The very phrase itself, "Pls send me the drake and ice spice leaks," found in online discussions, underscores a public appetite and demand for such content, regardless of its authenticity or ethical implications. The context of these discussions often points to the blurred lines between public and private. Consider the sentiment, "She say ice spice, what you doing? (what) I can take a shit and they view it (click) you didn't think I could do it my farts are more relevant than you is I'd lose anythin' before my man I'm a." While this specific quote might not directly describe the alleged **Ice Spice leak** content, it speaks volumes about the intrusive nature of public scrutiny and the perception that even the most mundane or personal aspects of a celebrity's life can become subjects of intense public interest and consumption. It reflects a cynical view where privacy is non-existent, and everything is fair game for public consumption, even if it's as trivial as a bodily function, as long as it generates "views" or "clicks." This attitude fuels the demand for "leaked" content, transforming private moments into public spectacle.The Digital Landscape and the Illusion of Privacy
The internet, particularly social media, has fundamentally reshaped our understanding of privacy. Platforms designed for sharing and connection inherently create vulnerabilities. "Most social media (and services that store images or videos for you) either can do this or do something pretty close," referring to the ability to store and potentially access user data, highlights a critical point: our digital lives are largely managed by third-party services. While these platforms have terms of service and privacy policies, the sheer volume of data they handle, combined with the constant threat of cyberattacks and internal breaches, means that personal information is never entirely secure. The illusion of privacy online is perpetuated by user-friendly interfaces that encourage constant sharing. Users often consent to broad data collection without fully understanding the implications. For public figures like Ice Spice, this vulnerability is amplified. Every post, every interaction, every piece of content they share, or that is shared about them, contributes to a vast digital footprint that can be exploited. Even content that is *not* shared by the individual themselves, but rather obtained through illicit means, becomes part of this public record, making the concept of an **Ice Spice leak** a constant threat in the digital age. The ease with which content can be copied, re-uploaded, and disseminated globally makes it virtually impossible to truly remove something once it's "out there."Celebrity Exploitation and Content Rights in the Digital Age
The entertainment industry has a long history of exploiting artists, and the digital age has introduced new, complex forms of this exploitation, particularly concerning content rights and personal image. The statement, "Based on the context, it sounds like Nicki might’ve had a deal like that early on with Wayne, and now that the roles are reversed, she expects Ice Spice to fork over rights too," sheds light on a pervasive issue: the pressure on emerging artists to cede control over their intellectual property and even their personal image in exchange for career advancement. This dynamic suggests a power imbalance where established figures or labels might demand rights to content that extends beyond music, potentially including personal likeness or even sensitive private material. For a rising star like Ice Spice, navigating these pressures while maintaining artistic integrity and personal boundaries is a monumental challenge. A "leak" in this context isn't just a breach of privacy; it can be a tool of control, a form of leverage, or a consequence of exploitative agreements. Artists, especially those at the beginning of their careers, may find themselves in situations where they feel compelled to compromise their privacy or control over their own narrative to achieve success. This highlights the urgent need for greater transparency and ethical standards in contracts within the entertainment industry, ensuring that artists, regardless of their fame level, retain fundamental rights over their personal content and image.The Role of Online Communities and Fan Culture
Online communities play a dual role in the phenomenon of "leaks." On one hand, they can be vibrant spaces for fan engagement, discussion, and support. Subreddits like `/r/h3h3productions`, which serves as "the home of the h3 podcast on reddit" and a place "for fans of the show to discuss recent episodes, share memes, suggest segments or interesting topics," exemplify how these platforms foster community and shared interest. Similarly, the "snl live discussion thread" creates a real-time communal viewing experience. These spaces are built on shared enthusiasm and open dialogue. However, this openness can also be a breeding ground for the spread of unverified information, rumors, and, unfortunately, leaked content. The existence of niche communities like "50 subscribers in the leeksarenotonions community" (even if satirical or unrelated to actual leaks, it highlights the existence of specific, often small, groups interested in niche content) or direct requests like "Pls send me the drake and ice spice leaks" demonstrate a darker side of online fan culture. In these environments, the desire for exclusive content, or simply the thrill of being "in the know," can override ethical considerations. The rapid sharing of content, often without critical evaluation of its source or legitimacy, contributes significantly to the virality of incidents like an alleged **Ice Spice leak**. These communities, while valuable for connection, also bear a responsibility to moderate content and discourage the dissemination of material that infringes on an individual's privacy or is obtained illicitly.Ethical Implications of Consuming Leaked Content
The consumption of leaked content, whether it pertains to an alleged **Ice Spice leak** or any other individual, raises significant ethical questions. When private photos, videos, or even unreleased music are disseminated without consent, it constitutes a profound violation of privacy and often a form of digital harassment. By viewing, sharing, or even just searching for such content, individuals inadvertently contribute to a harmful cycle. * **Violation of Autonomy:** Leaked content strips individuals of their right to control their own image and narrative. It denies them the choice of what to share and with whom. * **Harm to Reputation and Mental Health:** The public exposure of private moments can cause immense psychological distress, reputational damage, and long-term emotional trauma for the victim. For a public figure, this damage is amplified by the sheer scale of exposure. * **Normalization of Illicit Behavior:** Engaging with leaked content normalizes the act of illicitly obtaining and sharing private information. It sends a message that privacy violations are acceptable, or even desirable, if the subject is a public figure. * **Supporting Criminal Activity:** In many cases, obtaining and distributing leaked content is illegal. Consuming it, even passively, can be seen as indirectly supporting those who engage in such activities. The ethical stance should always prioritize the individual's right to privacy and dignity. Curiosity should not override respect for personal boundaries. As digital citizens, we have a collective responsibility to refuse to engage with, and actively report, content that appears to be a violation of someone's privacy.Legal Ramifications and Recourse for Victims
The legal landscape surrounding digital leaks is complex but increasingly robust. Illicitly obtaining and distributing private content, including in instances like an alleged **Ice Spice leak**, often falls under several legal categories: * **Copyright Infringement:** If the leaked material is original creative work (e.g., unreleased music, personal videos created by the individual), its unauthorized distribution can constitute copyright infringement. * **Invasion of Privacy:** Many jurisdictions recognize a right to privacy, and the non-consensual dissemination of private information or images can lead to civil lawsuits for invasion of privacy. * **Revenge Porn Laws:** In cases where sexually explicit material is shared without consent, many countries and states have specific "revenge porn" laws that criminalize such acts. * **Cyberstalking/Harassment:** Persistent sharing or malicious intent behind the leak can also fall under cyberstalking or harassment laws. Victims of leaks, including celebrities, have several avenues for recourse: * **Digital Millennium Copyright Act (DMCA) Takedowns:** Copyright holders can issue DMCA takedown notices to websites and platforms hosting infringing content, compelling them to remove it. * **Platform Reporting Mechanisms:** Social media platforms and content hosting sites typically have reporting mechanisms for privacy violations, harassment, and illegal content. While effectiveness varies, consistent reporting can lead to content removal and account suspension. * **Law Enforcement Involvement:** For serious cases, victims can report the incident to law enforcement, potentially leading to criminal investigations and charges against those responsible for the leak. * **Civil Lawsuits:** Victims can pursue civil lawsuits against individuals or entities responsible for the leak to seek damages for emotional distress, reputational harm, and financial losses. The legal system is slowly catching up to the pace of digital technology, but proactive measures and swift action are crucial for victims seeking to mitigate the damage caused by a privacy breach.Protecting Your Digital Footprint: Best Practices
While no digital footprint is entirely immune to compromise, individuals can take significant steps to protect their privacy and minimize the risk of being subjected to incidents like an **Ice Spice leak**. These practices are crucial for everyone, not just public figures: * **Strong, Unique Passwords:** Use complex, unique passwords for every online account. Consider a password manager to keep track of them. * **Two-Factor Authentication (2FA):** Enable 2FA wherever possible. This adds an extra layer of security, requiring a second verification step beyond just a password. * **Be Mindful of What You Share:** Think critically before posting anything online. Assume that anything you share could potentially become public. This includes seemingly private messages or content shared with a small group. * **Review Privacy Settings Regularly:** Periodically check and adjust the privacy settings on all social media platforms and apps. Understand who can see your posts, photos, and personal information. * **Be Wary of Phishing and Scams:** Be cautious of suspicious emails, messages, or links that ask for personal information or login credentials. These are common tactics used to gain unauthorized access to accounts. * **Secure Your Devices:** Use strong passcodes on your phone, tablet, and computer. Keep your operating systems and apps updated to benefit from the latest security patches. * **Understand App Permissions:** Before installing new apps, review the permissions they request. Does a flashlight app really need access to your contacts or camera? * **Limit Personal Information Online:** Avoid sharing sensitive personal details like your home address, exact birthdate, or financial information on public profiles. * **Educate Yourself:** Stay informed about common online threats and privacy best practices. The more you know, the better equipped you are to protect yourself. * **Consider Data Minimization:** Only provide the absolute necessary information when signing up for services. The less data stored about you, the less there is to potentially leak.Conclusion: Towards a More Responsible Digital Future
The discussions surrounding the alleged **Ice Spice leak** serve as a powerful microcosm of the larger challenges we face in the digital age: the erosion of privacy, the complexities of celebrity in a hyper-connected world, and the ethical responsibilities of online communities. It underscores that while technology offers unprecedented opportunities for connection and expression, it also presents significant vulnerabilities that demand our collective attention. Moving forward, it is imperative that we cultivate a more responsible digital culture. This means not only holding platforms and perpetrators accountable for privacy breaches but also empowering individuals with the knowledge and tools to protect their digital footprints. For consumers of online content, it means exercising critical judgment and choosing not to engage with material that violates an individual's privacy. For artists and public figures, it highlights the need for robust legal protections and ethical industry practices that safeguard their autonomy and personal well-being. Ultimately, the goal should be to foster an online environment where creativity can flourish without fear of exploitation, and where privacy is respected as a fundamental right, not a privilege. Let's engage in discussions that uplift and inform, rather than those that contribute to the spread of harmful or illicit content. Share this article to spark a conversation about digital privacy, and explore other resources on our site for more insights into navigating the complexities of the online world. Your informed choices contribute to a safer, more ethical digital future for everyone.
Ice Spice Leak Video 😭😭😭💦💦💦(Official Video) - YouTube
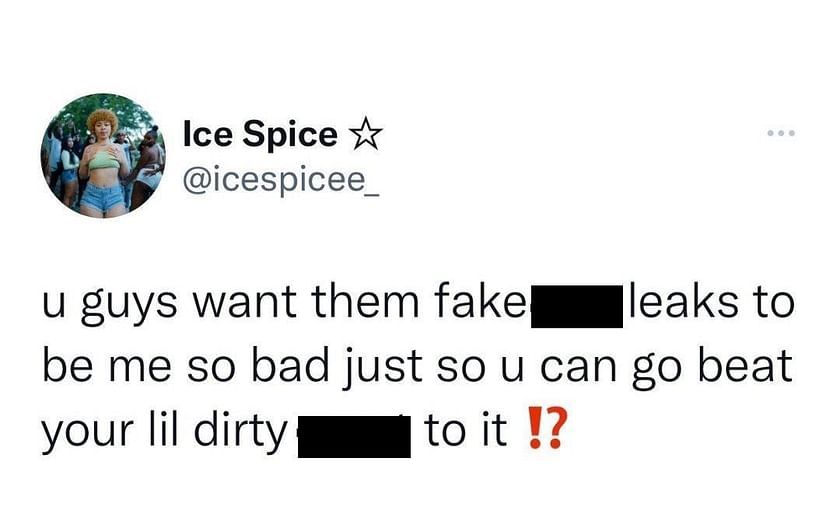
Ice Spice Twitter leak explained as rapper responds to alleged tape

How to watch Ice Spice Leak Video On Twitter | by Rozlandharbaughqx